Aws Cloud Backup Fundamentals Explained
The Ultimate Guide To Data Protection
Table of ContentsNot known Details About Ec2 Backup Aws Cloud Backup for BeginnersSome Ideas on Rto You Need To KnowThe Greatest Guide To Ec2 BackupThe Single Strategy To Use For Protection Against Ransomware
Keeping multiple suppliers and platforms along with common computer has actually put great stress on IT divisions. Going ahead, data protection must have the ability to adapt to these currently complicated situations. Information defense approaches are made to secure information, preserve personal privacy and also stop information loss and also corruption without trading them for analysis and testimonial.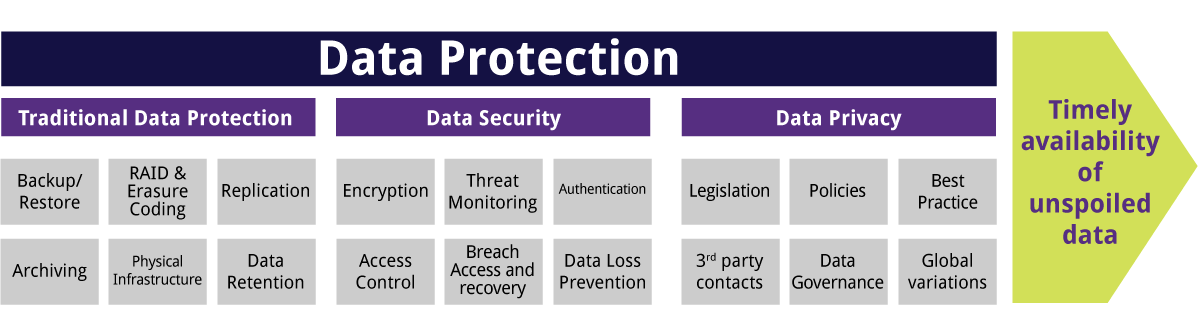
Information erasure techniques likewise verify the data can not be recovered. Accessibility monitoring manages make sure information stability by limiting access to electronic assets.
So a lot of the globe's interactions as well as organization happens in the cloud or through individual tools in remote work settings. The very best information security options combine robust safety measures with human processes and also workflows. The overall objective: to ensure data defense is considered early during the digital info life cycle.
Fascination About Aws S3 Backup
Data safety and security is every person's business, so, it's additionally essential to make certain routine, continuous safety recognition training is component of your information security strategy. Information privacy defines who has access to information, while information defense provides devices and also policies to actually restrict access to the data.
It plays a vital function in organization operations, advancement, and also finances. By safeguarding information, business can prevent data breaches, damages to online reputation, as well as can better satisfy governing requirements. Data security remedies depend on technologies such as information loss avoidance (DLP), storage with integrated data security, firewall programs, security, as well as endpoint security.
An information protection strategy is important for any kind of organization that gathers, manages, or stores sensitive data. Information security principles aid secure data and make it readily available under any kind of conditions.
Little Known Questions About Protection Against Ransomware.
Here are vital information administration facets appropriate to information security: making certain customers can access as well as make use of the data called for to carry out company also when this information is lost or harmed. involves automating the transmission of critical information to offline and online storage space. includes the appraisal, cataloging, as well as defense of info properties from numerous sources, consisting of facility blackouts and also disruptions, application and customer errors, device failure, and malware and virus assaults.
Information personal privacy is generally related to individual health and wellness info (PHI) and directly recognizable details (PII). This includes economic details, medical documents, social safety and security or ID numbers, names, birthdates, and visit contact info. Information privacy problems put on all delicate info that companies deal with, consisting of that of clients, shareholders, and staff members. Typically, this info plays an important duty in organization procedures, development, and also finances.
It stops bad guys from having the ability to maliciously use information and aids guarantee that companies meet regulative requirements. Information security policies control just how particular information kinds are gathered, sent, and also used. Personal data consists of various types of information, consisting of names, pictures, e-mail addresses, bank account information, IP addresses of desktop computers, and biometric information.

S3 Backup for Dummies
In addition, each regulation has many clauses that might put on one situation yet not another, and also all guidelines undergo changes. This degree of complexity makes it challenging to carry out conformity constantly and properly. Both information protection and also personal privacy are important and the two usually come with each other, these terms do not represent the exact same thing.
Information privacy defines the policies that information defense tools and also processes use. You can limit accessibility with information protections while still leaving delicate data susceptible.
For defense, it is up to the firms taking care of information to ensure that it remains personal. Conformity regulations mirror this difference and also are produced to help make sure that customers' personal privacy demands are established by business. When it comes to securing your data, there are numerous storage space as well as administration alternatives you can select from (s3 cloud backup).
Below are several of one of the most frequently utilized methods and also innovations: a primary step in data defense, this entails finding which data sets exist in the company, which of them are company important and also which consists of sensitive data that might be subject to conformity regulations (s3 cloud backup). a collection of approaches and tools that you can utilize to stop data from being taken, shed, or unintentionally removed.
All About Data Protection
Cloudian's Hyperstore supplies up to 14 nines of longevity, low price allowing storage of large quantities of information, as well as rapid access for marginal RTO/RPO. Discover a lot more in our guide to.